
Securing Your Web Applications: Advanced Techniques and Best Practices
Advanced web application security is becoming a crucial frontier in today’s digital world. Businesses are increasingly reliant on web applications that not only drive productivity but also hold sensitive data. But alongside these benefits lurk serious vulnerabilities and potential attack vectors. Here’s what you need to know at a glance:
- Importance: Protects against data breaches and maintains operational integrity.
- Vulnerabilities: Includes SQL injections, XSS, CSRF, XXE injections, and SSRF.
- Attack Vectors: Exploitable flaws through user inputs, URL parameters, database interaction, and more.
Web application security isn’t just about fixing bugs; it’s about building robust defenses from the start. As cybercriminals grow more sophisticated, employing advanced techniques and following best practices is essential to stay ahead.
At Amplify Score, we specialize in advanced web application security. From custom web development to cutting-edge AI tools and IT consulting, we’ve got the expertise to ensure your digital landscape is secure and optimized. Transitioning from outdated technology to secure systems is just the beginning.
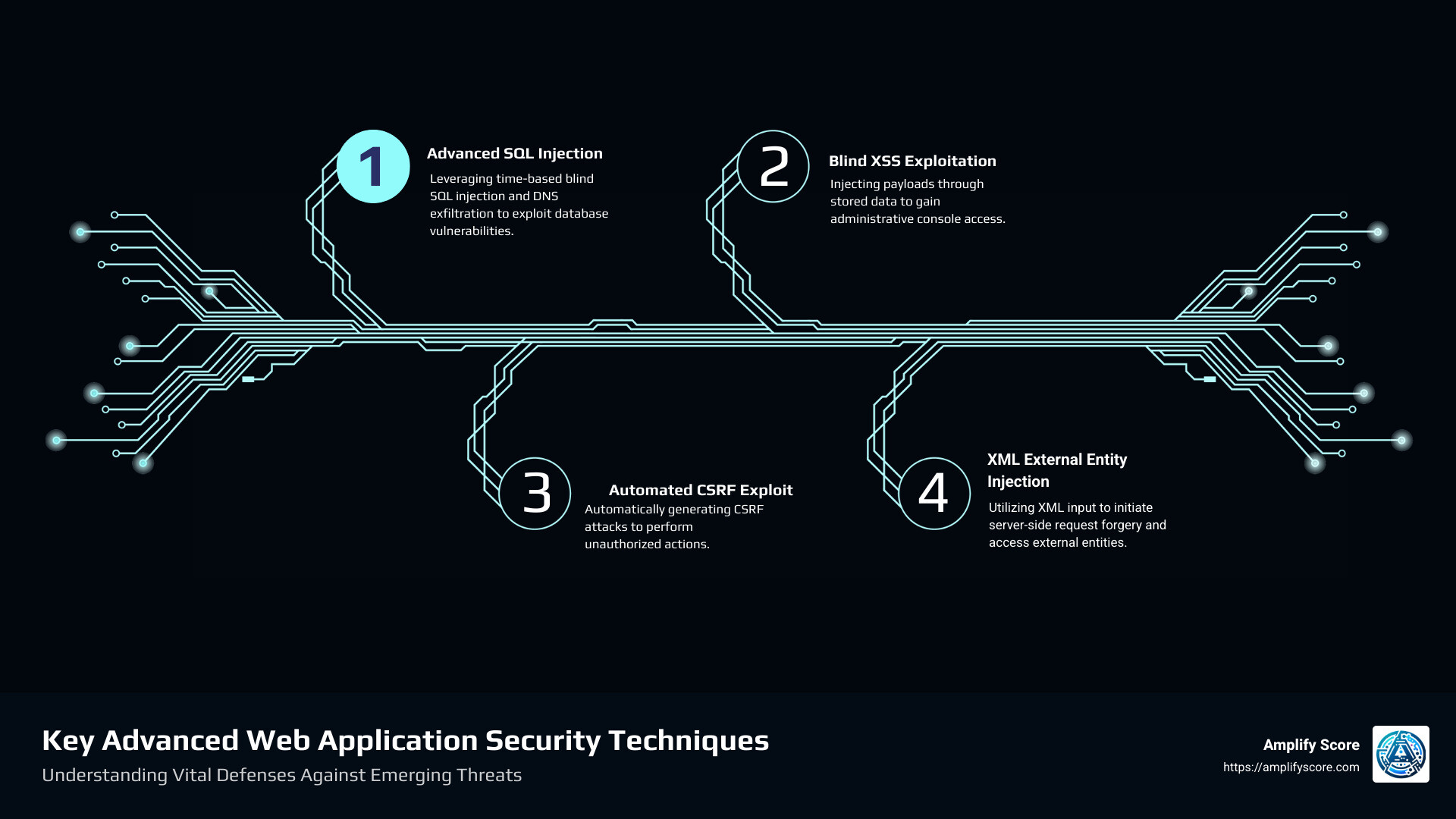
Key advanced web application security vocabulary:
Understanding Web Application Security
Web application security is all about making sure websites work as they should, even when someone tries to attack them. It’s like building a fortress around your web application to keep out the bad guys. But instead of bricks and mortar, we use security controls and secure development practices.
What is Web Application Security?
At its core, web application security involves integrating a series of protective measures into your web applications. These measures are designed to guard against malicious attacks and ensure that applications operate smoothly and securely.
Security Controls and the SDLC
Security controls are the tools and practices that protect your web applications. They are embedded throughout the software development life cycle (SDLC). Here’s how they fit into each phase:
- Planning: Identify potential risks and define security requirements.
- Design: Incorporate security features into the architecture.
- Implementation: Use secure coding practices to prevent vulnerabilities.
- Testing: Conduct security testing to find and fix vulnerabilities.
- Deployment: Ensure that security measures are in place and functioning.
- Maintenance: Regularly update and patch applications to address new threats.
Secure Development Practices
Secure development practices are essential to prevent vulnerabilities before they become a problem. These practices include:
- Input Validation: Ensure that all user inputs are checked for malicious content.
- Output Encoding: Safely encode data before displaying it to users.
- Authentication and Authorization: Verify the identity of users and control access to resources.
- Error Handling: Manage errors gracefully without exposing sensitive information.
Common Vulnerabilities
Despite best efforts, vulnerabilities can still creep into web applications. Some of the most common include:
- SQL Injection: Manipulating a database through user inputs.
- Cross-Site Scripting (XSS): Injecting malicious scripts into web pages.
- Cross-Site Request Forgery (CSRF): Trick users into performing unwanted actions.
- XML External Entity (XXE) Injection: Exploiting XML parsers to access sensitive data.
- Server-Side Request Forgery (SSRF): Sending unauthorized requests from the server.

By understanding and addressing these vulnerabilities, you can build more secure web applications. It’s not just about fixing issues as they arise but preventing them from occurring in the first place. This proactive approach is what sets advanced web application security apart.
Next, we’ll dig into why advanced web application security is crucial for your business, exploring risk assessment, compliance, and reputation protection.
Why Advanced Web Application Security is Crucial
In today’s digital landscape, securing your web applications is not just a technical necessity—it’s a business imperative. Let’s explore why advanced web application security is crucial by examining risk assessment, compliance, reputation protection, and a real-world case study.
Risk Assessment
Risk assessment is the first step in understanding the security needs of your web applications. It involves identifying potential threats and evaluating the impact they could have on your business. By understanding these risks, organizations can implement targeted security measures to protect against the most likely and damaging attacks.
Consider this: web applications are among the most potent attack surfaces that a cyber hacker can exploit. Ignoring these risks could lead to data breaches, financial loss, and damage to your business reputation.
Compliance
Compliance with industry regulations is another critical reason for prioritizing web application security. Many industries have specific standards that organizations must meet to protect sensitive data. For example, healthcare organizations must comply with HIPAA, while eCommerce businesses need to adhere to PCI DSS standards.
Failing to comply with these regulations can result in hefty fines and legal consequences. But beyond that, compliance demonstrates a commitment to protecting your clients’ data, which can improve trust and credibility.
Reputation Protection
A company’s reputation is one of its most valuable assets. A security breach can tarnish that reputation, leading to lost business and difficulty attracting new clients.
Downtime caused by a cyber threat can disrupt operations and erode customer trust. Once damaged, a reputation can be challenging to rebuild. Therefore, investing in advanced web application security is essential to safeguard your brand’s integrity.
Casio Case Study
Even large, established companies are not immune to web application attacks. Take Casio, for instance. Despite its size and resources, Casio experienced a significant web application breach. This incident serves as a stark reminder that no organization is too big to be targeted.
Casio’s experience underscores the importance of not underestimating the risk of an attack. It highlights the need for continuous security assessments and the implementation of advanced security measures to protect against evolving threats.
By prioritizing advanced web application security, businesses can mitigate risks, ensure compliance, and protect their reputation. Next, we’ll explore the advanced techniques used to secure web applications against sophisticated attacks.
Advanced Techniques for Web Application Security
In the field of advanced web application security, a variety of sophisticated techniques are employed to safeguard against complex threats. Let’s dig into these advanced methods and understand how they protect sensitive web applications.
Advanced SQL Injection Techniques
SQL injection remains a potent threat, allowing attackers to manipulate databases through seemingly innocent inputs. Time-based blind SQL injection is a method where attackers infer data by observing time delays in database responses. Another sophisticated technique is DNS exfiltration, where data is extracted by encoding it into DNS queries. These techniques highlight the importance of robust input validation and prepared statements to prevent unauthorized database access.
Blind XSS Exploitation
Blind Cross-Site Scripting (XSS) targets vulnerabilities that don’t provide immediate feedback to attackers. Malicious scripts are injected into stored data, later executed when accessed by users with higher privileges, such as administrators. This can lead to unauthorized actions within administrative consoles. Payloads crafted for blind XSS often “phone home” to alert attackers when triggered, making it crucial to sanitize all user inputs and outputs.
Automated CSRF Exploit Generation
Cross-Site Request Forgery (CSRF) tricks users into executing unauthorized actions on web applications where they are authenticated. Automated exploit generation streamlines the creation of CSRF attacks, simulating large-scale distribution of malicious requests. Ensuring proper CSRF tokens and validating request origins are essential defenses against such threats.
XML External Entity (XXE) Injection
XXE vulnerabilities exploit XML parsers by defining external entities linked to file URIs or server-controlled resources. This can lead to server-side request forgery (SSRF), data disclosure, or even remote code execution. Applications using XML inputs must configure parsers securely to prevent XXE attacks, especially when handling data from untrusted sources.
Server-Side Request Forgery (SSRF)
SSRF attacks trick servers into making requests to unintended locations, potentially accessing internal services or leaking sensitive data. This is especially dangerous in cloud environments, where internal services might lack authentication. Identifying and securing functionalities that make HTTP requests based on user input is key to mitigating SSRF risks.
WebSockets Hijacking and Testing
WebSocket vulnerabilities can lead to session hijacking and information leakage. Attackers exploit insecure implementations to intercept or manipulate communications between clients and servers. Testing for these vulnerabilities ensures that WebSocket communications remain secure from eavesdropping and tampering.
Advanced Brute-Force Techniques
Brute-force attacks have evolved to bypass traditional defenses like rate limiting. Attackers use distributed attacks from multiple IPs and employ machine learning to predict password patterns. Ensuring strong password policies and implementing multi-factor authentication can mitigate these sophisticated brute-force attempts.
Object Deserialization Exploits
Deserialization vulnerabilities arise when applications recreate objects from untrusted binary data. Attackers craft malicious serialized objects to execute arbitrary code during deserialization. Identifying and securing endpoints that accept serialized objects is vital to preventing such exploits.
Testing GraphQL and API Security
APIs, especially those using GraphQL, can expose excessive data if not properly secured. Testing for vulnerabilities ensures that APIs only expose intended data and functionality. Proper authentication, authorization, and query validation prevent unauthorized access and data leakage.
Container Escape and Docker Security Testing
Containerized environments like Docker must be secured to prevent “container escape” attacks. These attacks exploit vulnerabilities or misconfigurations to gain access to the host system or other containers. Regular security testing and adhering to best practices in container deployment can protect against such threats.
By employing these advanced techniques, organizations can bolster their web application defenses against sophisticated attacks. Up next, we’ll cover best practices for ensuring ongoing web application security.
Best Practices for Web Application Security
Securing web applications is more important than ever. Here, we’ll explore some best practices that can help you protect your web applications from potential threats.
Secure Coding
Secure coding is the backbone of advanced web application security. It means writing code that is free from vulnerabilities. By following secure coding guidelines, developers can prevent common issues like SQL injection and cross-site scripting (XSS). It’s crucial to regularly update coding practices to keep up with new threats.
Input Validation
Input validation is about ensuring that the data entered into your application is safe and expected. By validating inputs, you can prevent malicious data from causing harm. For example, if your application expects a number, make sure the input is a number and not a string of harmful code. This simple step can block many attacks before they start.
Output Encoding
Output encoding is a way to ensure that data is safely displayed to users. It involves converting data into a secure format before it is shown on a web page. This prevents attackers from injecting harmful scripts into the application. For example, converting special characters into HTML entities can stop XSS attacks.
Business Logic Security
Business logic security focuses on protecting the core operations of your application. This involves ensuring that the application behaves as intended, even when under attack. By understanding the business processes and identifying potential vulnerabilities, you can implement controls to prevent misuse. For instance, ensure that users can’t bypass critical steps in a transaction process.
By incorporating these best practices into your web development process, you can significantly reduce the risk of security breaches. Next, we’ll explore the importance of threat modeling in securing web applications.
Threat Modeling and Its Importance
Threat modeling is a proactive approach to identifying and addressing potential threats to your web application. It’s like creating a blueprint for security, ensuring that every aspect of your application is scrutinized for vulnerabilities.
Understanding Architecture and Data Flow
To effectively model threats, you need a deep understanding of your application’s architecture and data flow. This involves mapping out how data moves through your system, from user inputs to backend processes. By visualizing this flow, you can pinpoint where sensitive data might be exposed.
For example, if your application handles customer orders, examine how order information is processed and stored. Are there any unnecessary steps where data could be intercepted? Understanding these pathways helps in identifying weak spots.
Identifying Entry Points
Every web application has entry points—places where data enters or exits the system. These are prime targets for attackers. Threat modeling focuses on identifying these entry points and assessing their security.
Consider login forms, API endpoints, and user-generated content as potential entry points. Are they protected against common attacks like SQL injection or cross-site scripting (XSS)? Regularly reviewing and securing these points is crucial for maintaining robust security.
Prioritizing Risks
Not all threats are created equal. Threat modeling helps prioritize risks based on their potential impact and likelihood. This means focusing your efforts on the most critical vulnerabilities first.
For instance, if a vulnerability could lead to unauthorized access to sensitive user data, it should be addressed before a less critical issue, like a minor UI glitch. By prioritizing risks, you ensure that your resources are used efficiently to protect your application.
The Strategic Advantage
The primary advantage of threat modeling is its ability to make your security efforts more targeted. Instead of a broad, unfocused attempt to uncover vulnerabilities, threat modeling directs your attention to the areas most likely to be exploited by attackers. This strategic focus not only saves time and resources but also increases the chances of detecting critical vulnerabilities.
Threat modeling is an indispensable tool in the arsenal of advanced web application security. By understanding your application’s architecture, identifying entry points, and prioritizing risks, you can create a more secure environment for your users.
Next, we’ll address some frequently asked questions about advanced web application security.
Frequently Asked Questions about Advanced Web Application Security
What is web application security?
Web application security is all about making sure your web applications are safe from attacks. It involves using security controls to protect against malicious agents—those who try to exploit vulnerabilities in your applications. Think of it like building a digital fortress around your app to keep out the bad guys. This includes integrating security measures throughout the Software Development Life Cycle (SDLC) to catch flaws before they become a problem.
How much does OSCP certification cost?
The Offensive Security Certified Professional (OSCP) is a well-regarded certification for those looking to prove their skills in penetration testing. The OSCP comes as part of the PEN-200 course, which can be accessed through different learning paths like Learn One and Learn Unlimited. Pricing varies depending on the package you choose, with options that cater to different levels of access and support. It’s a worthwhile investment for anyone serious about a career in cybersecurity.
What does WAF do?
A Web Application Firewall (WAF) is a tool that protects web applications by filtering and monitoring HTTP traffic. It acts like a security guard for your web app, blocking suspicious activities such as cross-site forgery, XSS, and SQL injection attacks. By analyzing incoming traffic, a WAF can prevent these common threats from reaching your application, keeping your data and users safe. This is crucial for maintaining the integrity and availability of your web services.

By addressing these common questions, we hope to shed light on the importance and intricacies of advanced web application security. Next, we’ll dive into best practices for securing your web applications.
Conclusion
As we wrap up our exploration of advanced web application security, it’s clear that protecting web applications is more important than ever. Whether you’re a small business or a large corporation, the right strategies can safeguard your digital assets and your reputation.
At Amplify Score, we understand that every business has unique needs. That’s why we specialize in custom solutions that are custom to fit your specific requirements. Our expertise in bespoke website design and development ensures that your web applications are not only secure but also optimized for performance and user experience.
In addition to our development services, we offer expert IT consulting to help you steer the complexities of web security. Our team is ready to assist with everything from vulnerability assessments to implementing the latest security best practices. We believe in empowering businesses with the knowledge and tools they need to stay ahead of potential threats.
One of our standout features is our flexible payment terms (NET 30/60/90), which make it easier for businesses of all sizes to invest in top-notch security solutions without straining their budgets. This flexibility ensures that you can access the services you need, when you need them.
To learn more about how Amplify Score can help you secure your web applications, explore our web development services. We’re here to support your journey towards a safer, more secure digital presence.
